Rd Client Remote Desktop
Applies to: Windows 10, Windows 8.1, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2
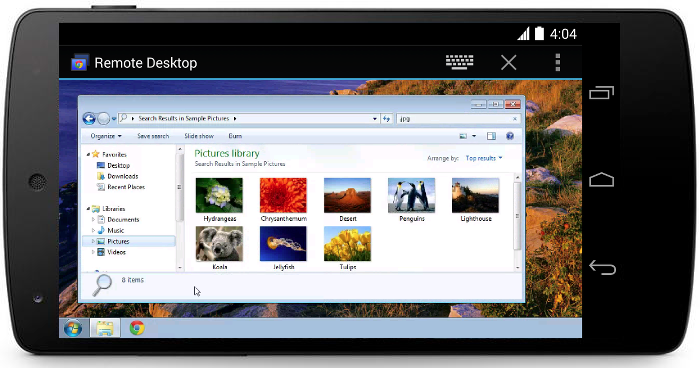
You can use the Remote Desktop client for iOS to work with Windows apps, resources, and desktops from your iOS device (iPhones and iPads).
Chrome Remote Desktop. Access my computer. Share my screen. The easy way to remotely connect with your home or work computer, or share your screen with others. Securely access your computer whenever you're away, using your phone, tablet, or another computer. However, the remote desktop client that Microsoft bundles with Windows leaves a lot to be desired. This is where RD Tabs comes in. RD Tabs is the original advanced multi-tabbed Windows Remote Desktop client and connection manager. It started back in 2006 with a simple idea: bring the then new idea of tabbed web browsers to remote desktop.
Use the following information to get started. Be sure to check out the FAQ if you have any questions.
Note
- Curious about the new releases for the iOS client? Check out What's new for Remote Desktop on iOS?.
- The iOS client supports devices running iOS 6.x and newer.
Get the Remote Desktop client and start using it
This section will tell you how to download and set up the Remote Desktop client for iOS.
Download the Remote Desktop client from the iOS store
First you'll need to download the client and configure your PC to connect to remote resources.
To download the client:
- Download the Microsoft Remote Desktop client from the iOS App Store or iTunes.
- Set up your PC to accept remote connections.
Add a PC
After you've downloaded the client and configured your PC to accept remote connections, it's time to actually add a PC.
To add a PC:
- In the Connection Center, tap +, then tap Add PC.
- Enter the following information:
- PC name – the name of the computer. The PC name can be a Windows computer name, an Internet domain name, or an IP address. You can also append port information to the PC name (for example, MyDesktop:3389 or 10.0.0.1:3389).
- User name – The user name you'll use to access the remote PC. You can use the following formats: user_name, domainuser_name, or
user_name@domain.com. You can also select Ask when required to be prompted for a user name and password when necessary.
- You can also set the following additional options:
- Friendly name (optional) – An easy-to-remember name for the PC you're connecting to. You can use any string, but if you don't specify a friendly name, the PC name is displayed instead.
- Gateway (optional) – The Remote Desktop gateway that you want to use to connect to virtual desktops, RemoteApp programs, and session-based desktops on an internal corporate network. Get the information about the gateway from your system administrator.
- Sound – Select the device to use for audio during your remote session. You can choose to play sound on the local devices, the remote device, or not at all.
- Swap mouse buttons – Whenever a mouse gesture would send a command with the left mouse button, it sends the same command with the right mouse button instead. Swapping mouse buttons is necessary if the remote PC is configured for left-handed mouse mode.
- Admin Mode - Connect to an administration session on a server running Windows Server 2003 or later.
- Clipboard - Choose whether to redirect text and images in your clipboard to your PC.
- Storage - Choose whether to redirect storage to your PC.
- Tap Save.
Need to edit these settings? Press and hold the desktop you want to edit, then tap the settings icon.
Add a workspace
To get a list of managed resources you can access on your iOS, add a workspace by subscribing to the feed provided by your admin.
To add a workspace:
- On the Connection Center screen, tap +, and then tap Add workspace.
- In the Feed URL field, enter the URL for the feed you want to add. This URL can be either a URL or an email address.
- If you use a URL, use the one your admin gave you.
- This URL is usually a Windows Virtual Desktop URL. Which one you use depends on which version of Windows Virtual Desktop you're using.
- For Windows Virtual Desktop (classic), use
https://rdweb.wvd.microsoft.com/api/feeddiscovery/webfeeddiscovery.aspx. - For Windows Virtual Desktop, use
https://rdweb.wvd.microsoft.com/api/arm/feeddiscovery.
- For Windows Virtual Desktop (classic), use
- This URL is usually a Windows Virtual Desktop URL. Which one you use depends on which version of Windows Virtual Desktop you're using.
- If you use an email address, enter your email address. Entering your email address tells the client ot search for a URL associated with your email address if your admin configured the server that way.
- If you use a URL, use the one your admin gave you.
- Tap Next.
- Provide your credentials when prompted.
- For User name, give the user name of an account with permission to access resources.
- For Password, give the password for the account.
- You may also be prompted to give additional information depending on the settings your admin configured authentication with.
- Tap Save.
After you've finished, the Connection Center should display the remote resources.
Once subscribed to a feed, the feed content will update automatically on a regular basis. Resources may be added, changed, or removed based on changes made by your administrator.
Manage your user accounts
When you connect to a PC or workspace, you can save the user accounts to select from again.
To create a new user account:
- In the Connection Center, tap Settings, and then tap User Accounts.
- Tap Add User Account.
- Enter the following information:
- User Name - The name of the user to save for use with a remote connection. You can enter the user name in any of the following formats:
user_name,domainuser_name, oruser_name@domain.com. - Password - The password for the user you specified.
- User Name - The name of the user to save for use with a remote connection. You can enter the user name in any of the following formats:
- Tap Save.
To delete a user account:
- In the Connection Center, tap Settings, and then tap User Accounts.
- Select the account you would like to delete.
- Tap Delete.
Connect to an RD Gateway to access internal assets
A Remote Desktop Gateway (RD Gateway) lets you connect to a remote computer on a corporate network from anywhere on the Internet. You can create and manage your gateways using the Remote Desktop client.
To set up a new gateway:
- In the Connection Center, tap Settings > Gateways.
- Tap Add gateway.
- Enter the following information:
- Gateway name – The name of the computer you want to use as a gateway. The gateway name can be a Windows computer name, an Internet domain name, or an IP address. You can also add port information to the server name (for example, RDGateway:443 or 10.0.0.1:443).
- User name - The user name and password to be used for the Remote Desktop gateway you're connecting to. You can also select Use connection credentials to use the same user name and password that you used for the remote desktop connection.
Navigate the Remote Desktop session
This section describes tools you can use to help navigate your Remote Desktop session.
Start a Remote Desktop connection
- Tap the remote desktop connection to start the remote desktop session.
- If you're asked to verify the certificate for the remote desktop, tap Accept. To accept by default, set Don't ask me again for connections to this computer to On.
Connection bar
The connection bar gives you access to additional navigation controls.
- Pan Control: The pan control enables the screen to be enlarged and moved around. Pan control is only available using direct touch.
- To enable or disable the pan control, tap the pan icon in the connection bar to display the pan control. The screen will zoom in while the pan control is active. the pan icon in the connection bar again to hide the control and return the screen to its original resolution.
- To use the pan control, tap and hold the pan control. While holding, drag your fingers in the direction you want to move the screen.
- To move the pan control, double-tap and hold the pan control to move the control on the screen.
- Connection name: The current connection name is displayed. Tap the connection name to display the session selection bar.
- Keyboard: Tap the keyboard icon to display or hide the keyboard. The pan control is displayed automatically when the keyboard is displayed.
- Move the connection bar: Tap and hold the connection bar. While holding the bar, drag it over to its new location. Let go of the bar to place it at the new location.
Session selection
You can have multiple connections open to different PCs at the same time. Tap the connection bar to display the session selection bar on the left-hand side of the screen. The session selection bar enables you to view your open connections and switch between them.
Here's what you can do with the session selection bar:
- To switch between apps in an open remote resource session, tap the expander menu and choose an app from the list.
- Tap Start New to start a new session, then choose a session from the list of available sessions.
- Tap the X icon on the left side of the session tile to disconnect from your session.
Command bar
The command bar replaced the Utility bar starting in version 8.0.1. You can use the command bar to switch between mouse modes and return to the connection center.
Use touch gestures and mouse modes in a remote session
The client uses standard touch gestures. You can also use touch gestures to replicate mouse actions on the remote desktop. The mouse modes available are defined in the table below.
Note
In Windows 8 or later, the native touch gestures are supported in Direct Touch mode. For more information on Windows 8 gestures, see Touch: Swipe, tap, and beyond.
| Mouse mode | Mouse operation | Gesture |
|---|---|---|
| Direct touch | Left-click | Tap with one finger |
| Direct touch | Right-click | Tap and hold with one finger |
| Mouse pointer | Left-click | Tap with one finger |
| Mouse pointer | Left-click and drag | Tap and hold with one finger, then drag |
| Mouse pointer | Right-click | Tap with two fingers |
| Mouse pointer | Right-click and drag | Double-tap and hold with two fingers, then drag |
| Mouse pointer | Mouse wheel | Double-tap and hold with two fingers, then drag up or down |
| Mouse pointer | Zoom | With two fingers, pinch to zoom out and spread fingers apart to zoom in |
Supported input devices
The client has Bluetooth mouse support for iOS 13 and iPadOS as an accessibility feature. You can use Swiftpoint GT or ProPoint mice for deeper mouse integration. The client also supports external keyboards that are compatible with iOS and iPadOS.
For more information about device support, see What's new in the iOS client and the iOS App Store.
Tip
Swiftpoint is offering an exclusive discount on the ProPoint mouse for iOS client users.
Use a keyboard in a remote session
You can use either an on-screen keyboard or physical keyboard in your remote session.
For on-screen keyboards, use the button on the right edge of the bar above the keyboard to switch between the standard and additional keyboard.
If Bluetooth is enabled on your iOS device, the client automatically detects the Bluetooth keyboard.
While certain key combinations might not work as expected in a remote session, many of the common Windows key combinations, such as CTRL+C, CTRL+V, and ALT+TAB will work.
Tip
Questions and comments are always welcome. However, if you post support requests or product feedback in this article's comments section, we won't be able to respond to your feedback. If you need help or want to troubleshoot your client, we highly recommend you go to the Remote Desktop client forum and start a new thread. If you have a feature suggestion, you can tell us using the Client UserVoice forum.
How secure is Windows Remote Desktop?
Remote Desktop sessions operate over an encrypted channel, preventing anyone from viewing your session by listening on the network. However, there is a vulnerability in the method used to encrypt sessions in earlier versions of RDP. This vulnerability can allow unauthorized access to your session using a man-in-the-middle attack.
Remote Desktop can be secured using SSL/TLS in Windows Vista, Windows 7, Windows 8, Windows 10 and Windows Server 2003/2008/2012/2016. *Some systems listed are no longer supported by Microsoft and therefore do not meet Campus security standards. If unsupported systems are still in use, a security exception is required.
While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
Basic Security Tips for Remote Desktop
1. Use strong passwords
Strong passwords on any accounts with access to Remote Desktop should be considered a required step before enabling Remote Desktop. Refer to the campus password complexity guidelines for tips.
2. Use Two-factor authentication
Departments should consider using a two-factor authentication approach. This topic is beyond the scope of this article, but RD Gateways can be configured to integrate with the Campus instance of DUO. Other unsupported by campus options available would be a simple mechanism for controlling authentication via two-factor certificate based smartcards. This approach utilizes the Remote Desktop host itself, in conjunction with YubiKey and RSA as examples.
3. Update your software
One advantage of using Remote Desktop rather than 3rd party remote admin tools is that components are updated automatically with the latest security fixes in the standard Microsoft patch cycle. Make sure you are running the latest versions of both the client and server software by enabling and auditing automatic Microsoft Updates. If you are using Remote Desktop clients on other platforms, make sure they are still supported and that you have the latest versions. Older versions may not support high encryption and may have other security flaws.
4. Restrict access using firewalls
Use firewalls (both software and hardware where available) to restrict access to remote desktop listening ports (default is TCP 3389). Using an RDP Gateway is highly recommended for restricting RDP access to desktops and servers (see discussion below). As an alternative to support off-campus connectivity, you can use the campus VPN software to get a campus IP address and add the campus VPN network address pool to your RDP firewall exception rule. Visit our page for more information on the campus VPN service.
5. Enable Network Level Authentication
Windows 10, Windows Server 2012 R2/2016/2019 also provide Network Level Authentication (NLA) by default. It is best to leave this in place, as NLA provides an extra level of authentication before a connection is established. You should only configure Remote Desktop servers to allow connections without NLA if you use Remote Desktop clients on other platforms that don't support it.
NLA should be enabled by default onWindows 10, Windows Server 2012 R2/2016/2019.
To check you may look at Group Policy setting Require user authentication for remote connections by using Network Level Authentication found at ComputerPoliciesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostSecurity. This Group Policy setting must be enabled on the server running the Remote Desktop Session Host role.
6. Limit users who can log in using Remote Desktop
By default, all Administrators can log in to Remote Desktop. If you have multiple Administrator accounts on your computer, you should limit remote access only to those accounts that need it. If Remote Desktop is not used for system administration, remove all administrative access via RDP, and only allow user accounts requiring RDP service. For Departments that manage many machines remotely remove the local Administrator account from RDP access at and add a technical group instead.
Click Start-->Programs-->Administrative Tools-->Local Security Policy
Under Local Policies-->User Rights Assignment, go to 'Allow logon through Terminal Services.' Or “Allow logon through Remote Desktop Services”
Remove the Administrators group and leave the Remote Desktop Users group.
Use the System control panel to add users to the Remote Desktop Users group.
A typical MS operating system will have the following setting by default as seen in the Local Security Policy:
The problem is that “Administrators” is here by default, and your “Local Admin” account is in administrators. Although a password convention to avoid identical local admin passwords on the local machine and tightly controlling access to these passwords or conventions is recommended, using a local admin account to work on a machine remotely does not properly log and identify the user using the system. It is best to override the local security policy with a Group Policy Setting.
To control access to the systems, even more, using “Restricted Groups” via Group Policy is also helpful.
If you use a “Restricted Group” setting to place your group, e.g., “CAMPUSLAW-TECHIES” into “Administrators” and “Remote Desktop Users,” your techies will still have administrative access remotely, but using the steps above, you have removed the problematic “local administrator account” having RDP access. Going forward, whenever new machines are added in the OU under the GPO, your settings will be correct.
7. Set an account lockout policy
By setting your computer to lock an account for a set number of incorrect guesses, you will help prevent hackers from using automated password guessing tools from gaining access to your system (this is known as a 'brute-force' attack). To set an account lockout policy:
- Go to Start-->Programs--> Administrative Tools--> Local Security Policy
- Under Account Policies--> Account Lockout Policies, set values for all three options. Three invalid attempts with 3-minute lockout durations are reasonable choices.
Best Practices for Additional Security
1. Do not allow direct RDP access to clients or servers from off campus.
Having RDP (port 3389) open to off campus networks is highly discouraged and is a known vector for many attacks. The options below list ways of improving security while still allowing RDP access to system.
Once an RDP gateway has been set up, hosts should be configured to only allow RDP connections from the Gateway host or campus subnets where needed.
2. Use RDP Gateways (Best Option)
Using an RDP Gateway is strongly recommended. It provides a way to tightly restrict access to Remote Desktop ports while supporting remote connections through a single 'Gateway' server. When using an RD Gateway server, all Remote Desktop services on your desktop and workstations should be restricted to only allow access only from the RD Gateway. The RD Gateway server listens for Remote Desktop requests over HTTPS (port 443) and connects the client to the Remote Desktop service on the target machine.
Utilize Campus RDP Gateway Service. This is the best option to allow RDP access to system categorized as UC P2 and lower. Includes DUO integration. RDP Gateway Service is provided by the Windows Team. Documentation is available here: https://berkeley.sharepoint.com/sites/calnetad/gateway.
The RDP Gateway Service also supports the new Remote Access Services requirement of the draft MSSND update (requirement 8), which requires the use of an approved service (i.e., RDP gateway, dedicated gateway, or bSecure VPN) for access to the UC Berkeley network from the public Internet.
Dedicated Gateway Service (Managed). Needed for rdp access to systems that are UC P4 or higher. Must also be configured for DUO
Some campus units use an IST managed VPS as an RD Gateway. A rough estimate might be that 30-100 concurrent users can use one RD Gateway. The HA at the virtual layer provides enough fault-tolerant and reliable access; however a slightly more sophisticated RD gateway implementation can be done with network load balancing.- Dedicated Gateway Service (Unmanaged). Installing and configuring RD Gateway on department run hardware.
There are many online documents for configuring this embedded Windows 2016/2019 component. The official documentation is here: https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-se...
Installing the configuring, the role service is mostly as described; however, using a Calnet issued trusted Comodo certificate is recommended. Using a self-signed cert is ok for testing, and using a CalnetPKI cert can work if all clients have trusted the UCB root. The Comodo cert is usually better accepted so that your end users do not receive certificate warnings.
Configuring your client to use your RD Gateway is simple.The official documentation for the MS Client is here: http://technet.microsoft.com/en-us/library/cc770601.aspx
Best Free Remote Desktop Software
In essence, a simple change on the advanced tab of your RDP client is all that is necessary:
3. Change the listening port for Remote Desktop
Changing the listening port will help to 'hide' Remote Desktop from hackers who are scanning the network for computers listening on the default Remote Desktop port (TCP 3389). This offers effective protection against the latest RDP worms such, as Morto. To do this, edit the following registry key (WARNING: do not try this unless you are familiar with the Windows Registry and TCP/IP): HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp. Change the listening port from 3389 to something else and remember to update any firewall rules with the new port. Although this approach is helpful, it is security by obscurity, which is not the most reliable security approach. You should ensure that you are also using other methods to tighten down access as described in this article.
4. Tunnel Remote Desktop connections through IPSec or SSH
If using an RD Gateway is not feasible, you can add an extra layer of authentication and encryption by tunneling your Remote Desktop sessions through IPSec or SSH. IPSec is built-in to all Windows operating systems since Windows 2000, but use and management are greatly improved in Windows 10 (see: http://technet.microsoft.com/en-us/network/bb531150). If an SSH server is available, you can use SSH tunneling for Remote Desktop connections.
5. Use existing management tools for RDP logging and configuration
Using other components like VNC or PCAnywhere is not recommended because they may not log in a fashion that is auditable or protected. With RDP, logins are audited to the local security log, and often to the domain controller auditing system. When monitoring local security logs, look for anomalies in RDP sessions such as login attempts from the local Administrator account. RDP also has the benefit of a central management approach via GPO as described above. Whenever possible, use GPOs or other Windows configuration management tools to ensure a consistent and secure RDP configuration across all your servers and desktops.
By enforcing the use of an RDP gateway, you also get a third level of auditing that is easier to read than combing through the domain controller logins and is separate from the target machine so it is not subject to tampering. This type of log can make it much easier to monitor how and when RDP is being used across all the devices in your environment.
Download Remote Desktop Windows 10
This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
